Gsm Key Generation And Encryption Process
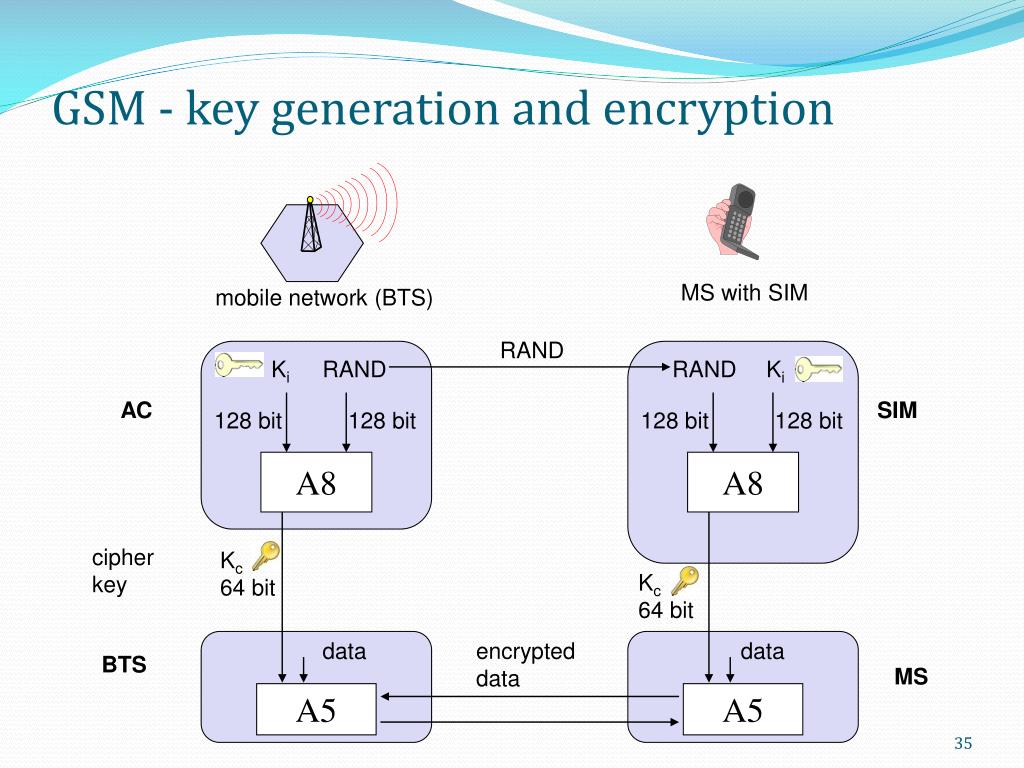
Authentication process helps gsm network authenticate the right user. This process is based on exchanged secret key Ki which is known to AuC (Authentication Center) and SIM card. There is no provision to read the key Ki from the SIM. This authentication procedure in gsm security mechanism is triggered due to following.
A variety of security algorithms are used to provide authentication, cipher key generation, integrity and radio link privacy to users on mobile networks. Details of the various algorithms and how they can be obtained are provided below. 3GPP Confidentiality and Integrity Algorithms 128-EEA3 & 128. Encryption is an essential part of a technology. It ensures the effective and secure authentication of users. A security algorithm is a mathematical procedure used to encrypt data. Information is encoded and requires the use of a software key to transform the data back into its original form. Our world-leading expertise in security algorithms. Oct 21, 2016 The encryption scheme used for second generation (2G) mobile phone data can be hacked within seconds by exploiting weaknesses and using common hardware, A.STAR. GSM modem is usually preferable to a GSM mobile phone. The GSM modem has wide range of applications in transaction terminals, supply chain management, security applications, weather stations and GPRS mode remote data logging. Working of GSM Module: From the below circuit, a GSM modem duly interfaced to the MC through the level shifter IC Max232. Security in GSM On air interface, GSM uses encryption and TMSI instead of IMSI. SIM is provided 4-8 digit PIN to validate the ownership of SIM 3 algorithms are specified: - A3 algorithm for authentication - A5 algorithm for encryption - A8 algorithm for key generation 21 NITIN PANDYA.
The call to ApiContext.create returns a singleton object of class ApiContext with the given CLIENTID and CLIENTSECRET, and will always return the same object even when called multiple times (even with a different CLIENTID and CLIENTSECRET). Java wrapper for Instamojo API Table of Contents.PrefaceInstamojo java wrapper for the Instamojo API assists you to programmatically create, list, filter payment orders andrefunds on Instamojo.  RequirementsJava Version: 1.7+ Installation GradleAdd following dependency to the build.gradlecompile group: 'com.instamojo', name: 'instamojo-java', version: '2.0.2' Authentication KeysGenerate CLIENTID and CLIENTSECRET for specific environments from the following links.Related support article: MultitenancyAs of now, MULTITENANCY IS NOT SUPPORTED by this wrapper which means you will not be able to use this wrapper in a single application with multiple Instamojo accounts.
RequirementsJava Version: 1.7+ Installation GradleAdd following dependency to the build.gradlecompile group: 'com.instamojo', name: 'instamojo-java', version: '2.0.2' Authentication KeysGenerate CLIENTID and CLIENTSECRET for specific environments from the following links.Related support article: MultitenancyAs of now, MULTITENANCY IS NOT SUPPORTED by this wrapper which means you will not be able to use this wrapper in a single application with multiple Instamojo accounts.
A5/1 is a stream cipher used to provide over-the-air communication privacy in the GSMcellular telephone standard. It is one of seven algorithms which were specified for GSM use.[1] It was initially kept secret, but became public knowledge through leaks and reverse engineering. A number of serious weaknesses in the cipher have been identified.
History and usage[edit]
A5/1 is used in Europe and the United States. A5/2 was a deliberate weakening of the algorithm for certain export regions.[2] A5/1 was developed in 1987, when GSM was not yet considered for use outside Europe, and A5/2 was developed in 1989. Though both were initially kept secret, the general design was leaked in 1994 and the algorithms were entirely reverse engineered in 1999 by Marc Briceno from a GSM telephone. In 2000, around 130 million GSM customers relied on A5/1 to protect the confidentiality of their voice communications; by 2014, it was 7.2 billion.[3]
Security researcher Ross Anderson reported in 1994 that 'there was a terrific row between the NATOsignal intelligence agencies in the mid-1980s over whether GSM encryption should be strong or not. The Germans said it should be, as they shared a long border with the Warsaw Pact; but the other countries didn't feel this way, and the algorithm as now fielded is a French design.'[4]
Description[edit]
A GSM transmission is organised as sequences of bursts. In a typical channel and in one direction, one burst is sent every 4.615 milliseconds and contains 114 bits available for information. A5/1 is used to produce for each burst a 114 bit sequence of keystream which is XORed with the 114 bits prior to modulation. A5/1 is initialised using a 64-bit key together with a publicly known 22-bit frame number. Older fielded GSM implementations using Comp128v1 for key generation, had 10 of the key bits fixed at zero, resulting in an effective key length of 54 bits. This weakness was rectified with the introduction of Comp128v3 which yields proper 64 bits keys. When operating in GPRS / EDGE mode, higher bandwidth radio modulation allows for larger 348 bits frames, and A5/3 is then used in a stream cipher mode to maintain confidentiality.
A5/1 is based around a combination of three linear feedback shift registers (LFSRs) with irregular clocking. The three shift registers are specified as follows:
| LFSR number | Length in bits | Feedback polynomial | Clocking bit | Tapped bits |
|---|---|---|---|---|
| 1 | 19 | 8 | 13, 16, 17, 18 | |
| 2 | 22 | 10 | 20, 21 | |
| 3 | 23 | 10 | 7, 20, 21, 22 |
The bits are indexed with the least significant bit (LSB) as 0.
The registers are clocked in a stop/go fashion using a majority rule. Each register has an associated clocking bit. At each cycle, the clocking bit of all three registers is examined and the majority bit is determined. A register is clocked if the clocking bit agrees with the majority bit. Hence at each step at least two or three registers are clocked, and each register steps with probability 3/4.
Initially, the registers are set to zero. Then for 64 cycles, the 64-bit secret key is mixed in according to the following scheme: in cycle , the ith key bit is added to the least significant bit of each register using XOR —
Each register is then clocked.
Similarly, the 22-bits of the frame number are added in 22 cycles. Then the entire system is clocked using the normal majority clocking mechanism for 100 cycles, with the output discarded. After this is completed, the cipher is ready to produce two 114 bit sequences of output keystream, first 114 for downlink, last 114 for uplink.
Security[edit]
A number of attacks on A5/1 have been published, and the American National Security Agency is able to routinely decrypt A5/1 messages according to released internal documents.[5]
Some attacks require an expensive preprocessing stage after which the cipher can be broken in minutes or seconds. Until recently, the weaknesses have been passive attacks using the known plaintext assumption. In 2003, more serious weaknesses were identified which can be exploited in the ciphertext-only scenario, or by an active attacker. In 2006 Elad Barkan, Eli Biham and Nathan Keller demonstrated attacks against A5/1, A5/3, or even GPRS that allow attackers to tap GSM mobile phone conversations and decrypt them either in real-time, or at any later time.
According to professor Jan Arild Audestad, at the standardization process which started in 1982, A5/1 was originally proposed to have a key length of 128 bits. At that time, 128 bits was projected to be secure for at least 15 years. It is now believed that 128 bits would in fact also still be secure until the advent of quantum computing. Audestad, Peter van der Arend, and Thomas Haug says that the British insisted on weaker encryption, with Haug saying he was told by the British delegate that this was to allow the British secret service to eavesdrop more easily. The British proposed a key length of 48 bits, while the West Germans wanted stronger encryption to protect against East German spying, so the compromise became a key length of 54 bits.[6]
Known-plaintext attacks[edit]
The first attack on the A5/1 was proposed by Ross Anderson in 1994. Anderson's basic idea was to guess the complete content of the registers R1 and R2 and about half of the register R3. In this way the clocking of all three registers is determined and the second half of R3 can be computed.[4]
In 1997, Golic presented an attack based on solving sets of linear equations which has a time complexity of 240.16 (the units are in terms of number of solutions of a system of linear equations which are required).
In 2000, Alex Biryukov, Adi Shamir and David Wagner showed that A5/1 can be cryptanalysed in real time using a time-memory tradeoff attack,[7] based on earlier work by Jovan Golic.[8] One tradeoff allows an attacker to reconstruct the key in one second from two minutes of known plaintext or in several minutes from two seconds of known plain text, but he must first complete an expensive preprocessing stage which requires 248 steps to compute around 300 GB of data. Several tradeoffs between preprocessing, data requirements, attack time and memory complexity are possible.
The same year, Eli Biham and Orr Dunkelman also published an attack on A5/1 with a total work complexity of 239.91 A5/1 clockings given 220.8 bits of known plaintext. The attack requires 32 GB of data storage after a precomputation stage of 238.[9]
Ekdahl and Johansson published an attack on the initialisation procedure which breaks A5/1 in a few minutes using two to five minutes of conversation plaintext.[10] This attack does not require a preprocessing stage. In 2004, Maximov et al. improved this result to an attack requiring 'less than one minute of computations, and a few seconds of known conversation'. The attack was further improved by Elad Barkan and Eli Biham in 2005.[11]
Attacks on A5/1 as used in GSM[edit]
In 2003, Barkan et al. published several attacks on GSM encryption.[12] The first is an active attack. GSM phones can be convinced to use the much weaker A5/2 cipher briefly. A5/2 can be broken easily, and the phone uses the same key as for the stronger A5/1 algorithm. A second attack on A5/1 is outlined, a ciphertext-only time-memory tradeoff attack which requires a large amount of precomputation.
In 2006, Elad Barkan, Eli Biham, Nathan Keller published the full version of their 2003 paper, with attacks against A5/X сiphers. The authors claim:[13]
We present a very practical ciphertext-only cryptanalysis of GSM encrypted communication, and various active attacks on the GSM protocols. These attacks can even break into GSM networks that use 'unbreakable' ciphers. We first describe a ciphertext-only attack on A5/2 that requires a few dozen milliseconds of encrypted off-the-air cellular conversation and finds the correct key in less than a second on a personal computer. We extend this attack to a (more complex) ciphertext-only attack on A5/1. We then describe new (active) attacks on the protocols of networks that use A5/1, A5/3, or even GPRS. These attacks exploit flaws in the GSM protocols, and they work whenever the mobile phone supports a weak cipher such as A5/2. We emphasize that these attacks are on the protocols, and are thus applicable whenever the cellular phone supports a weak cipher, for example, they are also applicable for attacking A5/3 networks using the cryptanalysis of A5/1. Unlike previous attacks on GSM that require unrealistic information, like long known plaintext periods, our attacks are very practical and do not require any knowledge of the content of the conversation. Furthermore, we describe how to fortify the attacks to withstand reception errors. As a result, our attacks allow attackers to tap conversations and decrypt them either in real-time, or at any later time.
In 2007 Universities of Bochum and Kiel started a research project to create a massively parallel FPGA-based cryptographic accelerator COPACOBANA. COPACOBANA was the first commercially available solution[14] using fast time-memory trade-off techniques that could be used to attack the popular A5/1 and A5/2 algorithms, used in GSM voice encryption, as well as the Data Encryption Standard (DES). It also enables brute force attacks against GSM eliminating the need of large precomputed lookup tables.
In 2008, the group The Hackers Choice launched a project to develop a practical attack on A5/1. The attack requires the construction of a large look-up table of approximately 3 terabytes. Together with the scanning capabilities developed as part of the sister project, the group expected to be able to record any GSM call or SMS encrypted with A5/1, and within about 3–5 minutes derive the encryption key and hence listen to the call and read the SMS in clear. But the tables weren't released.[15]
A similar effort, the A5/1 Cracking Project, was announced at the 2009 Black Hat security conference by cryptographers Karsten Nohl and Sascha Krißler. It created the look-up tables using NvidiaGPGPUs via a peer-to-peerdistributed computing architecture. Starting in the middle of September 2009, the project ran the equivalent of 12 Nvidia GeForce GTX 260. According to the authors, the approach can be used on any cipher with key size up to 64-bits.[16]
In December 2009, the A5/1 Cracking Project attack tables for A5/1 were announced by Chris Paget and Karsten Nohl. The tables use a combination of compression techniques, including rainbow tables and distinguished point chains. These tables constituted only parts of the 1.7 TB completed table and had been computed during three months using 40 distributed CUDA nodes and then published over BitTorrent and Google drive that is provided by community member Farid Nasiri [15][16][17][18][19] More recently the project has announced a switch to faster ATI Evergreen code, together with a change in the format of the tables and Frank A. Stevenson announced breaks of A5/1 using the ATI generated tables.[20]
Documents leaked by Edward Snowden in 2013 state that the NSA 'can process encrypted A5/1'.[21]
See also[edit]
- KASUMI, also known as A5/3
Notes[edit]
- ^'Prohibiting A5/2 in mobile stations and other clarifications regarding A5 algorithm support'.
- ^Quirke, Jeremy (1 May 2004). 'Security in the GSM system'(PDF). AusMobile. Archived from the original(PDF) on 12 July 2004. Retrieved 8 September 2008.
- ^'There are officially more mobile devices than people in the world'. The Independent. 7 October 2014. Retrieved 19 December 2017.
- ^ abRoss Anderson (17 June 1994). 'A5 (Was: HACKING DIGITAL PHONES)'. Newsgroup: uk.telecom. Usenet:2ts9a0$95r@lyra.csx.cam.ac.uk.
- ^NSA Able To Crack A5/1 Cellphone Crypto - Slashdot
- ^http://www.aftenposten.no/nyheter/uriks/Sources-We-were-pressured-to-weaken-the-mobile-security-in-the-80s-7413285.html#.UtBeNpD_sQs
- ^Biryukov, Alex; Adi Shamir; David Wagner. 'Real Time Cryptanalysis of A5/1 on a PC'. Fast Software Encryption—FSE 2000: 1–18.
- ^Golic, Jovan Dj. (1997). 'Cryptanalysis of Alleged A5 Stream Cipher'(PDF). Eurocrypt 1997: 239–55. Archived from the original(PDF) on 15 July 2010. Retrieved 13 January 2016.
- ^Biham, Eli; Orr Dunkelman (2000). 'Cryptanalysis of the A5/1 GSM Stream Cipher'. Indocrypt 2000. Lecture Notes in Computer Science. 1977: 43–51. doi:10.1007/3-540-44495-5_5. ISBN978-3-540-41452-0.
- ^Ekdahl, Patrik; Thomas Johansson (2003). 'Another attack on A5/1'(PDF). IEEE Transactions on Information Theory. 49 (1): 284–89. doi:10.1109/TIT.2002.806129. Archived from the original(PDF) on 25 May 2005.
- ^Barkan, Elad; Eli Biham (2005). 'Conditional Estimators: An Effective Attack on A5/1'. Selected Areas in Cryptography 2005: 1–19.
- ^Barkan, Elad; Eli Biham; Nathan Keller (2003). 'Instant Ciphertext-Only Cryptanalysis of GSM Encrypted Communication'(PDF). Crypto 2003. Lecture Notes in Computer Science. 2729: 600–16. doi:10.1007/978-3-540-45146-4_35. ISBN978-3-540-40674-7.
- ^Barkan, Elad; Eli Biham; Nathan Keller. 'Instant Ciphertext-Only Cryptanalysis of GSM Encrypted Communication by Barkan and Biham of Technion (Full Version)'(PDF).
- ^Gueneysu, Tim; Timo Kasper; Martin Novotný; Christof Paar; Andy Rupp (2008). 'Cryptanalysis with COPACOBANA'(PDF). IEEE Transactions on Computers. 57 (11): 1498–1513. doi:10.1109/TC.2008.80.
- ^ abNohl, Karsten; Chris Paget (27 December 2009). GSM: SRSLY?. 26th Chaos Communication Congress (26C3). Archived from the original on 6 January 2010. Retrieved 30 December 2009.
- ^ ab'Archived copy'(PDF). Archived from the original(PDF) on 26 July 2011. Retrieved 29 December 2009.CS1 maint: archived copy as title (link) Subverting the security base of GSM. Karsten Nohl and Sascha Krißler
- ^O'Brien, Kevin (28 December 2009). 'Cellphone Encryption Code Is Divulged'. New York Times. Archived from the original on 29 April 2011. Retrieved 29 December 2009.
- ^McMillan, Robert. 'Hackers Show It's Easy to Snoop on a GSM Call'. IDG News Service.
- ^Nohl, Karsten. 'Direct Link A5/1 rainbow Table in Google drive'.
- ^Frank A. Stevenson (1 May 2010). 'Cracks beginning to show in A5/1'. Archived from the original on 6 March 2012.
- ^Timberg, Craig; Soltani, Ashkan (13 December 2013). 'By cracking cellphone code, NSA has ability to decode private conversations'. The Washington Post. Retrieved 28 September 2016.
References[edit]
- Rose, Greg (10 September 2003). 'A precis of the new attacks on GSM encryption'(PDF). QUALCOMM Australia.
- Maximov, Alexander; Thomas Johansson; Steve Babbage (2004). 'An Improved Correlation Attack on A5/1'. Selected Areas in Cryptography 2004: 1–18.
External links[edit]
- Briceno, Marc; Ian Goldberg; David Wagner (23 October 1999). 'A pedagogical implementation of the GSM A5/1 and A5/2 'voice privacy' encryption algorithms'.
- 'Huge GSM flaw allows hackers to listen in on voice calls'. 25 August 2009. Archived from the original on 14 October 2009.
- Horesh, Hadar (3 September 2003). 'Technion team cracks GSM cellular phone encryption'(PDF). Haaretz.
- Barkan, Elad; Eli Biham; Nathan Keller (July 2006). 'Instant Ciphertext-Only Cryptanalysis of GSM Encrypted Communication (Technical Report CS-2006-07)'.
- 'Nathan Keller's Homepage'. Archived from the original on 4 June 2008.
- 'Animated SVG showing A5/1 stream cypher'. Archived from the original on 26 March 2012.
GSM is a mobile communication modem; it is stands for global system for mobile communication (GSM). The idea of GSM was developed at Bell Laboratories in 1970. It is widely used mobile communication system in the world. GSM is an open and digital cellular technology used for transmitting mobile voice and data services operates at the 850MHz, 900MHz, 1800MHz and 1900MHz frequency bands.
GSM system was developed as a digital system using time division multiple access (TDMA) technique for communication purpose. A GSM digitizes and reduces the data, then sends it down through a channel with two different streams of client data, each in its own particular time slot. The digital system has an ability to carry 64 kbps to 120 Mbps of data rates.
There are various cell sizes in a GSM system such as macro, micro, pico and umbrella cells. Each cell varies as per the implementation domain. There are five different cell sizes in a GSM network macro, micro, pico and umbrella cells. The coverage area of each cell varies according to the implementation environment.
Time Division Multiple Access
TDMA technique relies on assigning different time slots to each user on the same frequency. It can easily adapt to data transmission and voice communication and can carry 64kbps to 120Mbps of data rate.
GSM Architecture
A GSM network consists of the following components:
- A Mobile Station: It is the mobile phone which consists of the transceiver, the display and the processor and is controlled by a SIM card operating over the network.
- Base Station Subsystem: It acts as an interface between the mobile station and the network subsystem. It consists of the Base Transceiver Station which contains the radio transceivers and handles the protocols for communication with mobiles. It also consists of the Base Station Controller which controls the Base Transceiver station and acts as a interface between the mobile station and mobile switching centre.
- Network Subsystem: It provides the basic network connection to the mobile stations. The basic part of the Network Subsystem is the Mobile Service Switching Centre which provides access to different networks like ISDN, PSTN etc. It also consists of the Home Location Register and the Visitor Location Register which provides the call routing and roaming capabilities of GSM. It also contains the Equipment Identity Register which maintains an account of all the mobile equipments wherein each mobile is identified by its own IMEI number. IMEI stands for International Mobile Equipment Identity.
Features of GSM Module:
- Improved spectrum efficiency
- International roaming
- Compatibility with integrated services digital network (ISDN)
- Support for new services.
- SIM phonebook management
- Fixed dialing number (FDN)
- Real time clock with alarm management
- High-quality speech
- Uses encryption to make phone calls more secure
- Short message service (SMS)
The security strategies standardized for the GSM system make it the most secure telecommunications standard currently accessible. Although the confidentiality of a call and secrecy of the GSM subscriber is just ensured on the radio channel, this is a major step in achieving end-to- end security.
GSM Modem

A GSM modem is a device which can be either a mobile phone or a modem device which can be used to make a computer or any other processor communicate over a network. A GSM modem requires a SIM card to be operated and operates over a network range subscribed by the network operator. It can be connected to a computer through serial, USB or Bluetooth connection.
A GSM modem can also be a standard GSM mobile phone with the appropriate cable and software driver to connect to a serial port or USB port on your computer. GSM modem is usually preferable to a GSM mobile phone. The GSM modem has wide range of applications in transaction terminals, supply chain management, security applications, weather stations and GPRS mode remote data logging.
Working of GSM Module:
Gsm Key Generation And Encryption Process Problems
From the below circuit, a GSM modem duly interfaced to the MC through the level shifter IC Max232. The SIM card mounted GSM modem upon receiving digit command by SMS from any cell phone send that data to the MC through serial communication. While the program is executed, the GSM modem receives command ‘STOP’ to develop an output at the MC, the contact point of which are used to disable the ignition switch. The command so sent by the user is based on an intimation received by him through the GSM modem ‘ALERT’ a programmed message only if the input is driven low. The complete operation is displayed over 16×2 LCD display.
Intelligent GSM Device for Automation and Security
Gsm Key Generation And Encryption Process Pdf
In these days, the GSM mobile terminal has become one of the items that are constantly with us. Just like our wallet/purse, keys or watch, the GSM mobile terminal provides us a communication channel that enables us to communicate with the world. The requirement for a person to be reachable or to call anyone at any time is very appealing.
In this project, as the name says project is based on GSM network technology for transmission of SMS from sender to receiver. SMS sending and receiving is used for ubiquitous access of appliances and allowing breach control at home. The system proposes two sub-systems. Appliance control subsystem enables the user to control home appliances remotely and the security alert subsystem gives the automatic security monitoring.
The system is capable enough to instruct user via SMS from a specific cell number to change the condition of the home appliance according to the user’s needs and requirements. The second aspect is that of security alert which is achieved in a way that on the detection of intrusion, the system allows automatic generation of SMS thus alerting the user against security risk.
Circuit Representation of Intelligent GSM Device for Automation and Security:
GSM will allow communication anywhere, anytime, and with anyone. The functional architecture of GSM employing intelligent networking principles, and its ideology, which provides the development of GSM is the first step towards a true personal communication system that enough standardization to ensure compatibility.
Photo Credit
Farming simulator 2013 product key generator free download full. Our key generator got tons of downloads in short time.Farming Simulator 2013 keygen is a succes, we guarantee that you will be pleased with itDownload now and share it with your friends! The more activation keys means the more people can enjoy the game for free.If you have generated a license key for yourself no one will be able to get that cd key again – it is like buying the game product key, you own Farming Simulator 2013 CD Key, but you do not have to pay a great deal of cash for it. Farming Simulator 2013 Gameplay Video TrailerYou don’t need Farming Simulator 2013 crack or any other Farming Simulator 2013 patch.Newest method which will bring you free cd key – product code without having to spend anything!! Yeah all keys generated with just one click.Please ensure that you have.net Framework 4.5 installed and internet access.
- GMS Modem by ggpht